What is Spear Phishing?
Spear Phishing is an attack technique in which an attacker crafts an e-mail using customized information about the recipient with the goal of tricking the recipient into divulging sensitive information such as usernames, passwords, credit card details, etc, or enticing the recipient to click a link that may introduce maliciously coded programs, such as spyware to their computer. The spear phishing e-mail usually will appear to come from a trusted identity, such as a familiar individual or business. It will contain information that the reader can relate to and can even be very specific to the reader’s personal life or business dealings, based on data the attacker has ascertained about the individual. The e-mail will usually contain links where the link text appears to be a familiar website, however the underlying URL (universal resource locator) actually links to a different site. For example http://www.KnownBank.com can actually point to http://FooledYouBank.com. It is best practice not to click on links embedded in e-mails unless you are absolutely sure that they are valid links. These type of attacks are becoming increasingly common as potential attackers have access to high-quality customized information that can be used to target unwitting, susceptible individuals.
Example of Spear Phishing E-mail
Below is an example of a spear phishing attack that I received today. It appears to be from Apple, an organization I have done business with. It speaks specifically about purchases through iTunes, a product I use regularly to purchase Apps, Music and other media. It also entices me to click the link for fear that an invalid purchase has been made with my Apple account.
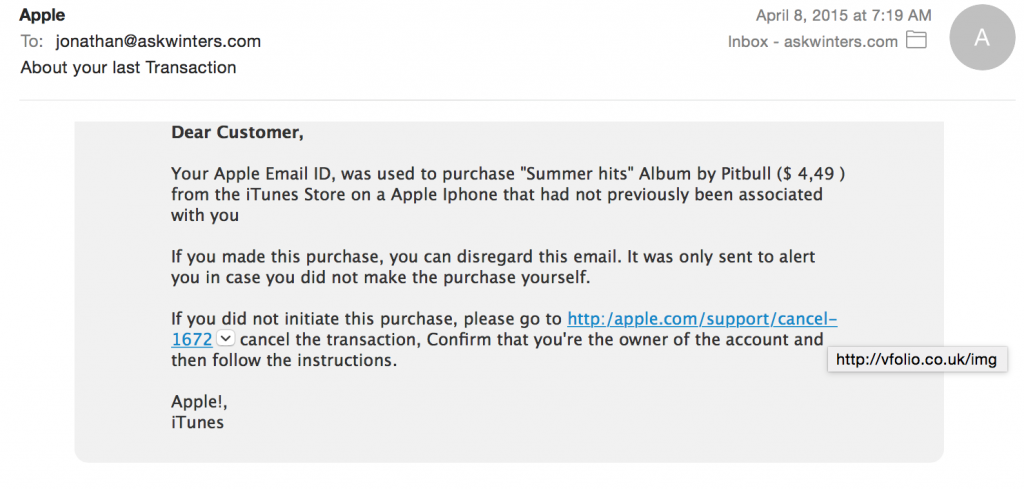
However, after a cursory look, you can plainly see that it is a malicious e-mail. When I hovered over the embedded link, it clearly pointed to a different address than the displayed text. When reviewing your own e-mails, if you are unsure of an e-mail’s validity, ask your local technology representative or geek friend to look at the underlying code of the e-mail to make a determination. Reminder, best practice is to never click on links that are received via email unless you are positive they lead to valid URLs.
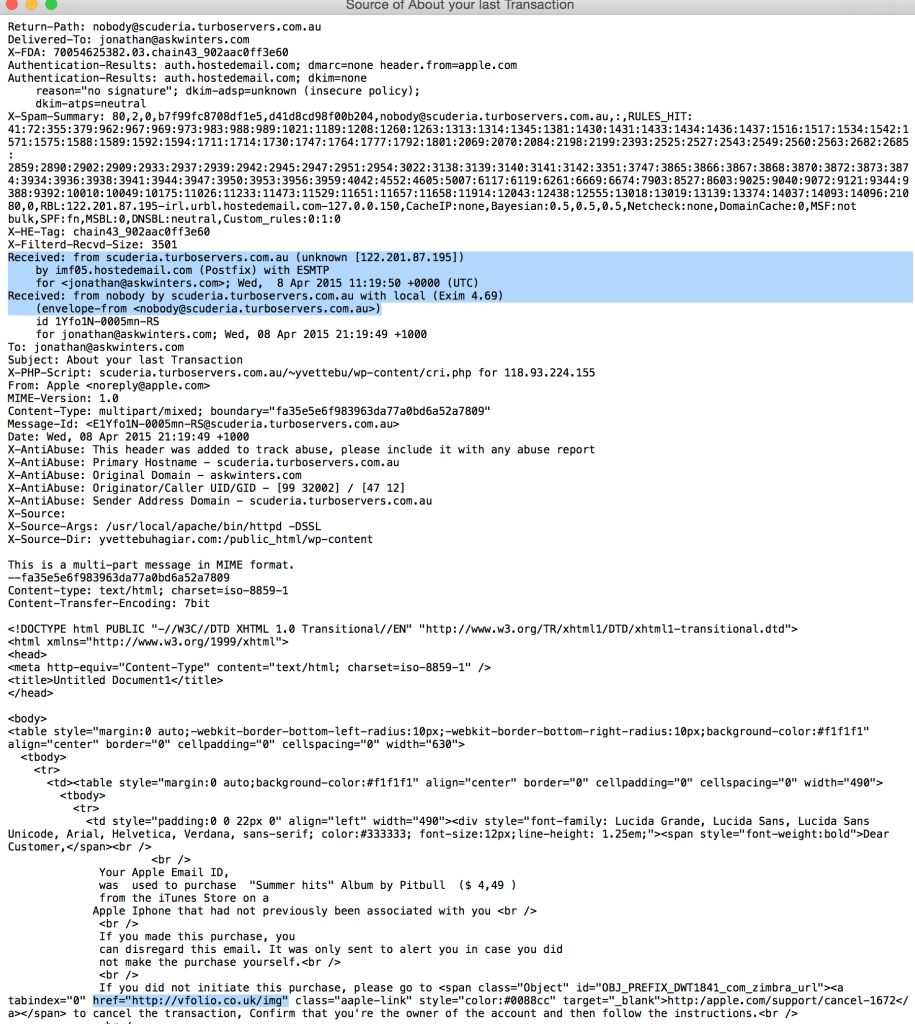
Technical Exploration of Underlying E-mail Code
Below is the underlying code of the email message displayed above. The first blue highlight indicates the sending server. Clearly this message did not originate from Apple.com. The second blue highlight indicates the underlying hyperlink reference, and again, clearly this does not link to Apple.com.