Many businesses, non-profit organizations and universities, across the planet, have networked IoT (Internet of Things) devices such as IP cameras, NVR (Network Video Recorder) systems, sensor devices, door access systems, or other such devices within their internal networks that are used for conducting their core business or research or monitoring and managing buildings.
One major use case where port forwarding is commonly used is when setting up viewing ingress of company premises video surveillance systems from outside of the business network. Most frequently, low voltage technicians are hired to deploy small or even large scale video surveillance equipment. Low voltage technicians usually are only trained in running physical, low voltage, network (Cat 5/Cat6) cable and basic system setup. Keep in mind, the low-volt technicians are often the same individuals or companies that deploy door/building access systems, time-clock systems, etc. If they merely stick to doing what they know and are not of the learning mentality, pursuing continuing education, they may not even be aware that their deployments may be subject to attack. Herein lies the problem, instead of learning and using network security best practices, they do what they know, simple port forwarding to the surveillance equipment, often without updating firmware or even changing default administrative passwords. Additionally, these deployments often do not have the network administrative security such as VLANs and firewalls. In addition to not following the administrative best practices, if the software running on these units has a zero-day or other such software vulnerability, this may also be an attack vector, as was the case with the HIKVISION hack a few years ago. By enabling unrestricted port forwarding the integrator may be unwittingly allowing anyone from the public Internet to access the recordings, and worse yet, other networked devices internal to the organization’s network.
Furthermore, if sufficient network border, network segmentation or ISP upstream security is not put in place, hackers or even script kiddies, are able to discover the vulnerability by simply running network port scans across public IP addresses and ports, potentially easily interacting with the administrative console of the system. This is the crux of this article, simply put, if the ports are forwarded, unrestricted, to the internal devices, from the public Internet, hackers may not even need to compromise a firmware or software vulnerability in the systems, they may be able to merely try the default passwords. If that doesn’t work, the attackers can begin to deploy a exploits against a known or unknown vulnerability in the service. Then, having direct ingress to this exposed system the attacker may now have the ability to enable network connection services such as SSH, or other such shell protocols. With shell access to a computer software based system on a company network, a hacker can begin executing commands or potentially deploying additional attack software directly from within the company network. This would be considered a type of beachhead attack. This attack could easily be avoided if proper understanding and due diligence is performed, configuring appropriate network rules for access to such IoT devices and systems.
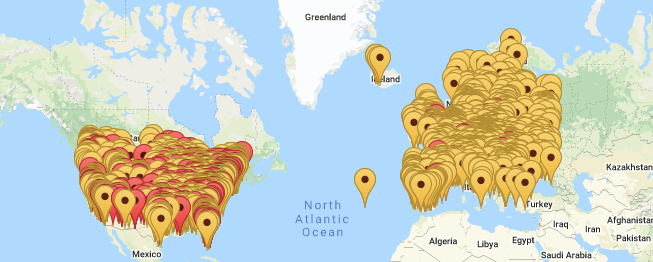
To illustrate the severity of this kind of reconfiguration, one such real world example of this type of vulnerability was demonstrated when IPVM published a map of hacked HIKVISION brand cameras in the USA and Europe in 2018. The interactive map, linked here illustrates the severity of such reconfiguration.
The takeaway here is thoroughly vet individuals and service providers who do this kind of work. Make sure they take into account best practices (article on best practices coming soon.)